Basic Recursive Caching DNS Server, Imagine it might be like if we needed recall IP addresses of all web sites that we use each day basis. Even if we had prodigious memory, the method to browse to a internet site might be ridiculously slow and time-ingesting.
if we needed recall IP addresses of all the web sites that we use on a each day basis. Even if we had prodigious memory, the method to browse to a internet site might be ridiculously slow and time-ingesting.
And what approximately if we had to go to a couple of websites or use several packages that reside in the same machine or digital host? That would be one of the worst complications I can consider – not to say the possibility that the IP deal with associated with a internet site or application can be modified with out earlier word.
DNS
Just the very thought of it might be sufficient purpose to desist the usage of the Internet or inner networks after a while. That’s precisely what a global without Domain Name System (additionally known as DNS) might be. Fortunately, this provider solves all of the troubles noted above the connection among an IP cope with name modifications. For that cause, in this text we are able to learn how to configure and use a simple DNS server, a provider so one can allow to translate domains into IP addresses and vice versa.
Introducing DNS Name Resolution
For small networks that aren’t difficulty to common changes, the /and many others/hosts document may be used as a rudimentary approach of domain call to IP deal with resolution.
With a totally simple syntax, this file allows us to accomplice a name with an IP cope with as follows:
[IP address] [name] [alias(es)]For example,
192.168.0.1 gateway gateway.mydomain.com
192.168.0.2 web web.mydomain.comThus, you could attain the internet device both by its name, the net.Mydomain.Com alias, or its IP cope with.
For larger networks, or those which can be concern to common adjustments, the usage of the /and so forth/hosts file to clear up domain names into IP addresses could not be a suitable answer.
That’s wherein the need for a dedicated service comes in.
Under the hood, a DNS server queries a massive database inside the shape of a tree, which begins at the root (“.”) zone.
The following image will assist us to demonstrate:
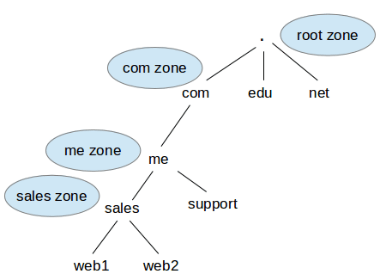
In the image above, the root (.) area consists of com, edu, and net domains. Each of those domain names are managed by way of special groups to avoid relying on a big, principal one. This lets in to correctly distribute requests in a hierarchical manner.
Let’s see what happens beneath the hood:
- When a purchaser makes a query to a DNS server for web1.Sales.Me.Com, the server sends the question to the pinnacle DNS server, which factors the question to the call server in the .Com area.
This, in turn, sends the query to the next degree name server (in the me.Com sector), and then to income.Me.Com.
This method is repeated as regularly as wanted until the FQDN is again by way of the name server of the sector where it belongs.
- In this situation, the call server in income.Me.Com. Responds for the deal with web1.Sales.Me.Com and returns the desired domain name-IP affiliation and other information as well (if configured to achieve this).
All this facts is despatched to the original DNS server, which then passes it lower back to the client that requested it within the first region.
To avoid repeating the equal steps for future identical queries, the results of the query are saved inside the DNS server.
These are the motives why this sort of setup is typically known as a recursive, caching DNS server.
Installing and Configuring a DNS Server
Basic Recursive Caching DNS Server,In Linux, the most used DNS server is bind, which may be established as follows:
# yum install bind bind-utils [CentOS]
# zypper install bind bind-utils [openSUSE]
# aptitude install bind9 bind9utils [Ubuntu]Once we have installed bind and related utilities, let’s make a copy of the configuration file before making any changes:
# cp /etc/named.conf /etc/named.conf.orig [CentOS and openSUSE]
# cp /etc/bind/named.conf /etc/bind/named.conf.orig [Ubuntu]Then let’s open named.Conf and head over to the alternatives block, in which we need to set make sure the subsequent settings are present to configure a recursive, caching server with IP 192.168.0.18/24 that can be accessed simplest by way of hosts in the identical community.
The forwarders settings are used to suggest which call servers ought to be queried first for hosts outside our area:
options {
...
listen-on port 53 { 127.0.0.1; 192.168.0.18};
allow-query { localhost; 192.168.0.0/24; };
recursion yes;
forwarders {
8.8.8.8;
8.8.4.4;
};
…
}Outside the alternatives block we will outline our income.Me.Com area that maps a site with a given IP deal with and a reverse quarter to map the IP cope with to the corresponding domain.
However, the actual configuration of every area will pass in separate files as indicated by means of the report directive.
Add the following blocks to named.Conf file:
zone "sales.me.com." IN {
type master;
file "/var/named/sales.me.com.zone";
};
zone "0.168.192.in-addr.arpa" IN {
type master;
file "/var/named/0.162.198.in-addr.arpa.zone";
};Note that in-addr.arpa (for IPv4 addresses) and ip6.arpa (for IPv6) are conventions for reverse zone configurations.
After saving the above changes to named.conf, we can check for errors as follows:
# named-checkconf /etc/named.confIf any errors are determined, the above command will output an informative message with the purpose and the road in which they are placed.
Otherwise, it’s going to no longer go back anything.
Basic Recursive Caching DNS Server,Configuring DNS Zones
In the files /var/named/sales.me.com.zone and /var/named/0.168.192.in-addr.arpa.zone we will configure the forward (domain → IP address) and reverse (IP address → domain) zones.
Let’s tackle the ahead configuration first:
- At the pinnacle of the document you may find a line beginning with TTL (short for Time To Live), which specifies how long the cached response should “live” earlier than being changed by using the consequences of a new query.
In the road immediately below, we will reference our domain and set the e-mail address where notifications need to be despatched (be aware that the foundation.Sales.Me.Com means [email protected]).
- A SOA (Start Of Authority) document indicates that this device is the authoritative nameserver for machines inside the income.Me.Com domain.
The following settings are required when there are two nameservers (one master and one slave) consistent with domain (although such isn’t always our case since it isn’t always required in the exam, they’re offered here in your reference):
The Serial is used to distinguish one version of the area definition document from a previous one (wherein settings ought to have modified). If the cached response factors to a definition with a extraordinary serial, the question is finished once more as opposed to feeding it lower back to the consumer.
In setup with a slave nameserver, Refresh indicates quantity time till secondary need to test a brand new serial from master server.
In addition,
Retry tells the server how often the secondary have to try and contact the number one if no response from the number one has been acquired, while Expire shows when the area definition inside the secondary is now not legitimate after the grasp server could not be reached, and Negative TTL is the time that a Non-existent area ought to be cached.
- A NS document suggests what’s the authoritative DNS server for our domain (referenced by using the @ sign at the start of the line).
- An A report (for IPv4 addresses) or an AAAA (for IPv6 addresses) interprets names into IP addresses.
In the instance underneath:
dns: 192.168.0.18 (the DNS server itself)
web1: 192.168.0.29 (a web server inside the sales.me.com zone)
mail1: 192.168.0.28 (a mail server inside the sales.me.com zone)
mail2: 192.168.0.30 (another mail server)- A MX record indicates the names of the authorized mail transfer marketers (MTAs) for this domain. The hostname should be prefaced with the aid of various indicating the concern that the current mail server ought to have while there are two or greater MTAs for the domain (the decrease the cost, the better the priority – in the following instance, mail1 is the number one whereas mail2 is the secondary MTA).
- A CNAME record units an alias (www.Web1) for a number (web1).
IMPORTANT: The dot (.) at the end of the names is required.
$TTL 604800
@ IN SOA sales.me.com. root.sales.me.com. (
2016051101 ; Serial
10800 ; Refresh
3600 ; Retry
604800 ; Expire
604800) ; Negative TTL
;
@ IN NS dns.sales.me.com.
dns IN A 192.168.0.18
web1 IN A 192.168.0.29
mail1 IN A 192.168.0.28
mail2 IN A 192.168.0.30
@ IN MX 10 mail1.sales.me.com.
@ IN MX 20 mail2.sales.me.com.
www.web1 IN CNAME web1Let’s now check the reverse area configuration (/var/named/zero.168.192.In-addr.Arpa.Zone).
The SOA record is similar to within the preceding file, while the closing three lines with a PTR (pointer) file suggest the closing octet inside the IPv4 address of the mail1, web1, and mail2 hosts (192.168.Zero.28, 192.168.0.29, and 192.168.0.30, respectively).
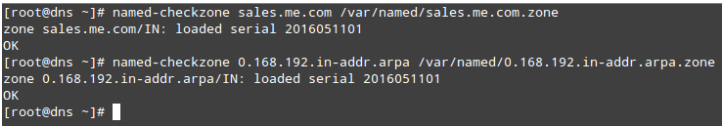
Let’s now check the reverse area configuration (/var/named/zero.168.192.In-addr.Arpa.Zone). The SOA record is similar to within the preceding file, while the closing three lines with a PTR (pointer) file suggest the closing octet inside the IPv4 address of the mail1, web1, and mail2 hosts (192.168.Zero.28, 192.168.0.29, and 192.168.0.30, respectively).You can check the zone files for errors with:
# named-checkzone sales.me.com /var/named/sales.me.com.zone
# named-checkzone 0.168.192.in-addr.arpa /var/named/0.168.192.in-addr.arpa.zoneThe following image illustrates what is the expected output on success:
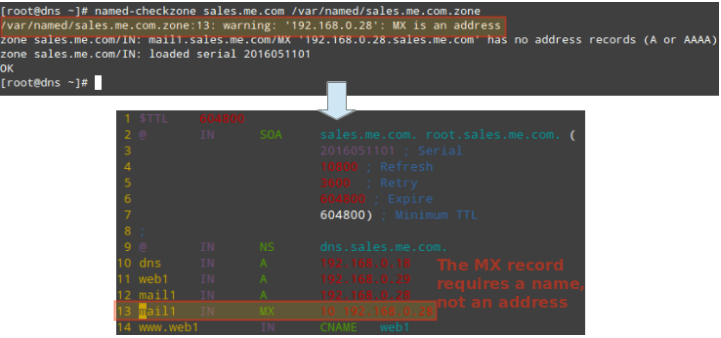
Otherwise, you will get an error message stating the cause and how to fix it:
Once you have verified the main configuration file and the zone files, restart the named service to apply changes.
In CentOS and openSUSE, do:
# systemctl restart namedAnd don’t forget to enable it as well:
# systemctl enable namedIn Ubuntu:
$ sudo service bind9 restartFinally, you will have to edit the configuration of your main network interfaces:
---- In /etc/sysconfig/network-scripts/ifcfg-enp0s3 for CentOS and openSUSE ----
DNS1=192.168.0.18
---- In /etc/network/interfaces for Ubuntu ----
dns-nameservers 192.168.0.18 and restart the network service to apply changes.
Testing the DNS Server
At this factor we are geared up to question our DNS server for nearby and outside names and addresses. The following commands will go back the IP deal with related to the host web1:
# host web1.sales.me.com
# host web1
# host www.web1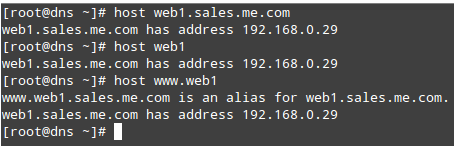
How can we find out who is handling emails for sales.me.com? It’s easy to find out – just query the MX records for the domain:
# host -t mx sales.me.com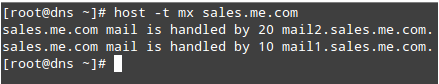
Likewise, let’s perform a reverse query. This will help us find out the name behind an IP address:
# host 192.168.0.28
# host 192.168.0.29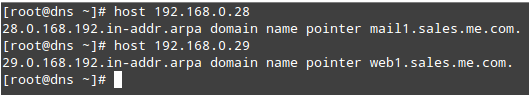
You can try the same operations for outside hosts:
# host -t mx linux.com
# host 8.8.8.8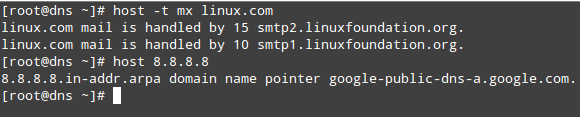
To verify that queries are indeed going through our DNS server, let’s enable logging:
# rndc querylogAnd check the /var/log/messages file (in CentOS and openSUSE):
# host -t mx linux.com
# host 8.8.8.8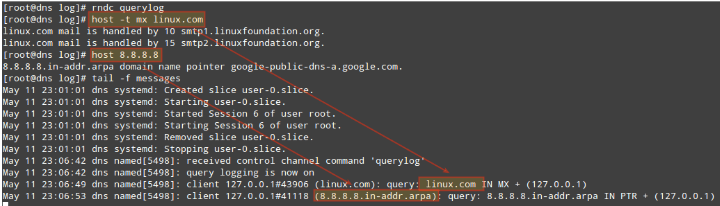
To disable DNS logging, type again:
# rndc querylogIn Ubuntu, enabling logging will require adding the following independent block (same level as the options block) to /etc/bind/named.conf:
logging {
channel query_log {
file "/var/log/bind9/query.log";
severity dynamic;
print-category yes;
print-severity yes;
print-time yes;
};
category queries { query_log; };
};Note that the log file must exist and be writable by named.
SUMMARY