Linux firewalls,about iptables and firewalld
Here’s how to use the iptables and firewalld tools to manage Linux firewall connectivity rules.
Linux firewalls,This article is excerpted from my book, Linux in Action, and a 2d Manning task that’s yet to be released.
Linux firewalls,The firewall
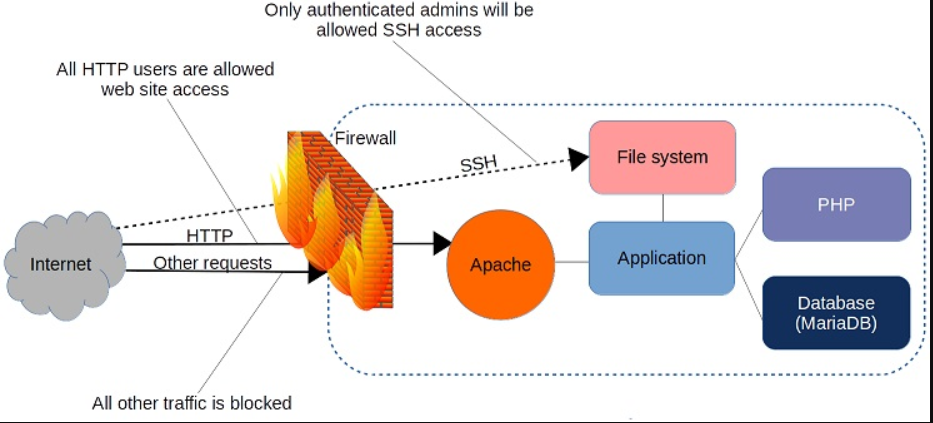
A firewall is a hard and fast of guidelines. When a facts packet actions into or out of a protected network space, its contents (especially, statistics approximately its beginning, target, and the protocol it plans to apply) are examined towards the firewall guidelines to see if it ought to be allowed via. Here’s a simple instance:
On the only hand, iptables is a tool for coping with firewall rules on a Linux gadget.
On the opposite hand, firewalld is likewise a tool for coping with firewall policies on a Linux gadget.
You got a trouble with that? And would it damage your day if I told you that there was some other device available, known as nftables?
Linux firewall connectivity rules.
OK, I’ll admit that the entirety does odor a piece funny, so allow me provide an explanation for. It all starts offevolved with Netfilter, which controls get entry to to and from the community stack at the Linux kernel module level. For decades, the number one command-line tool for coping with Netfilter hooks turned into the iptables ruleset.
Because the syntax needed to invoke the ones guidelines ought to come across as a bit arcane, numerous user-friendly implementations like ufw and firewalld were added as higher-degree Netfilter interpreters. Ufw and firewalld are, however, in general designed to clear up the types of troubles faced by using stand-on my own computers. Building full-sized community solutions will often require the extra muscle of iptables or, since 2014, its replacement, nftables (through the nft command line device). Iptables hasn’t long gone everywhere and is still widely used. In fact, you must assume to run into iptables-included networks to your work as an admin for decades to return. But nftables, by means of adding on to the classic Netfilter toolset, has added some critical new functionality.
From right here on, I’ll display by means of instance how firewalld and iptables solve simple connectivity issues.
Linux firewalls,Configure HTTP access using firewalld
As you would possibly have guessed from its name, firewalld is a part of the systemd own family. Firewalld may be installed on Debian/Ubuntu machines, but it’s there by using default on Red Hat and CentOS. If you’ve were given a web server like Apache strolling to your gadget,
you could verify that the firewall is running by using browsing on your server’s net root. If the website online is unreachable, then firewalld is doing its task.
You’ll use the firewall-cmd tool to manipulate firewalld settings from the command line. Adding the –kingdom argument returns the modern firewall status:
# firewall-cmd –state running
By default, firewalld could be energetic and will reject all incoming visitors with more than one exceptions, like SSH. That manner your internet site received’t be getting too many visitors, to be able to sincerely save you a number of data transfer expenses. As that’s in all likelihood not what you had in thoughts to your web server, though,
you’ll want to open the HTTP and HTTPS ports that with the aid of conference are specific as 80 and 443, respectively. Firewalld gives two approaches to do that. One is thru the –add-port argument that references the port range directly along with the community protocol it’ll use (TCP in this situation). The –everlasting argument tells firewalld to load this rule on every occasion the server boots:
Configure HTTP access using firewalld
# firewall-cmd –permanent –add-port=80/tcp # firewall-cmd –permanent –add-port=443/tcp
The –reload argument will observe those regulations to the cutting-edge consultation:
# firewall-cmd –reload
Curious as to the modern settings on your firewall? Run –listing-offerings:
# firewall-cmd –list-services dhcpv6-client http https ssh
Assuming you’ve brought browser get admission to as described earlier, the HTTP, HTTPS, and SSH ports have to now all be open—in conjunction with dhcpv6-customer,
which lets in Linux to request an IPv6 IP address from a neighborhood DHCP server.
Configure a locked-down customer kiosk using iptables
I’m certain you’ve seen kiosks—they’re the tablets, touchscreens, and ATM-like PCs in a field that airports, libraries, and business leave lying round,
inviting customers and passersby to browse content material. The thing approximately most kiosks is which you don’t generally need users to make themselves at home and treat them like their personal devices. They’re now not generally meant for browsing, viewing YouTube films, or launching denial-of-service attacks against the Pentagon. So to ensure they’re no longer misused, you need to lock them down.
One manner is to apply a few sort of kiosk mode, whether or not it’s via smart use of a Linux display supervisor or at the browser stage. But to ensure you’ve got all of the holes plugged,
you’ll in all likelihood also need to add some difficult community controls thru a firewall. In the following segment, I’ll describe how I could do it using iptables.
There are critical matters to remember approximately using iptables: The order you supply your rules is critical, and by way of themselves, iptables rules won’t continue to exist a reboot. I’ll deal with those right here one at a time.
Linux firewalls,The kiosk project
To illustrate all this, permit’s believe we paintings for a store that’s a part of a larger chain called BigMart. They’ve been around for decades; in reality, our imaginary grandparents likely grew up purchasing there. But nowadays,
the guys at BigMart company headquarters are probably just counting the hours before Amazon drives them under for properly.
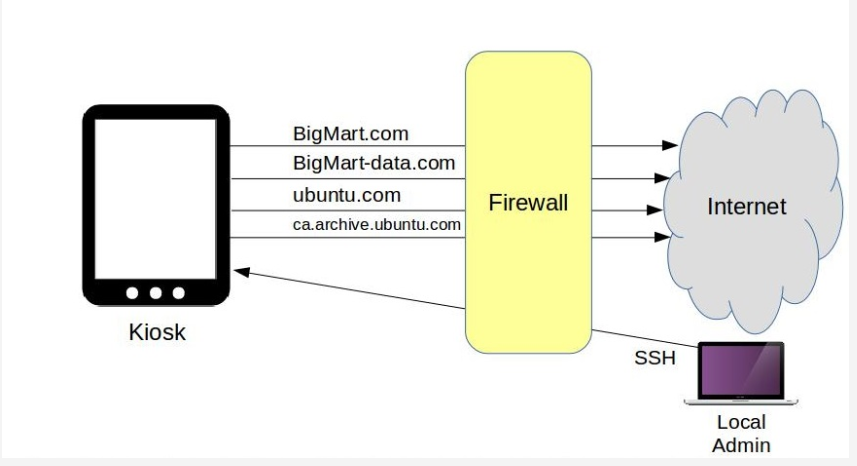
Nevertheless, BigMart’s IT department is doing its satisfactory, and they’ve just despatched you some WiFi-ready kiosk gadgets which you’re predicted to install at strategic places during your keep. The idea is they’ll display an internet browser logged into the BigMart.Com merchandise pages,
allowing them to look up merchandise features, aisle area, and stock ranges. The kiosks may even need access to bigmart-records.Com, where most of the photos and video media are stored.
Besides those, you’ll need to permit updates and, every time vital, bundle downloads. Finally,
you’ll want to allow inbound SSH get entry to most effective out of your neighborhood laptop, and block all people else. The discern below illustrates how it’ll all work:

Linux firewalls,The script
Here’s how so as to all match right into a Bash script:
#!/bin/bash
iptables -A OUTPUT -p tcp -d bigmart.com -j ACCEPT
iptables -A OUTPUT -p tcp -d bigmart-data.com -j ACCEPT
iptables -A OUTPUT -p tcp -d ubuntu.com -j ACCEPT
iptables -A OUTPUT -p tcp -d ca.archive.ubuntu.com -j ACCEPT
iptables -A OUTPUT -p tcp --dport 80 -j DROP
iptables -A OUTPUT -p tcp --dport 443 -j DROP
iptables -A INPUT -p tcp -s 10.0.3.1 --dport 22 -j ACCEPT
iptables -A INPUT -p tcp -s 0.0.0.0/0 --dport 22 -j DROP