Create a more secure automated system

SSH Key Authentication, If you’re a Linux administrator, then you definitely are very familiar with the ssh command. Why? Because it’s far the maximum popular way of getting access to a far off Linux server. Out of the box, Secure Shell (SSH) is regularly considered quite comfortable. If you’re extreme approximately your protection, however, you understand that to be a slight exaggeration. Yes, SSH is a way higher than the use of a maximum different way of remotely logging into a Linux server. If used accurately, it may be made even greater relaxed. How? With SSH Key Authentication.
What is SSH Key Authentication?
Normally, whilst you log right into a faraway server with SSH, you achieve this the use of a username/password aggregate. Issue the command:
ssh [email protected]You’ll be caused by the consumer password for Olivia. That’s the most often used technique for SSH logins. However, the use of a password is restricted to the duration of the password you may do not forget, or are inclined to type out. Sure, you could have a person Olivia set a password that’s incredibly lengthy and complex but is that user going to need to type that password each time they want to log in? Probably no longer. With SSH Key Authentication, an encrypted passphrase is used that is a long way longer than is sensible with a popular password. So the cryptographic strength observed in SSH Key Authentication goes manner past that which a popular password can suit.
But to use SSH Key Authentication, you have to set it up. Fortunately, it’s especially easy to do.
Generating Your SSH Key
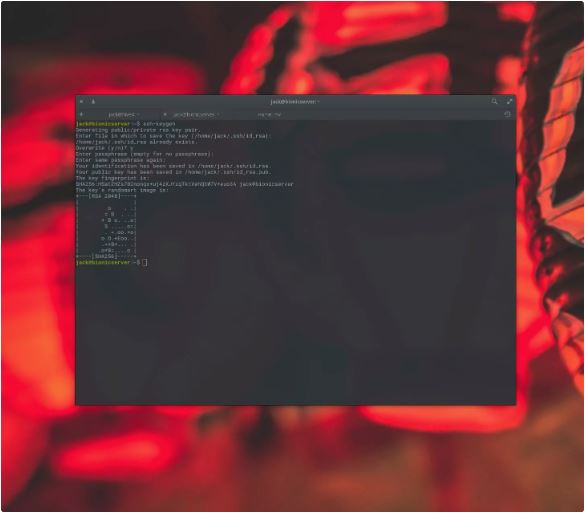
The first factor you ought to do is generate an SSH Key. This is quite clean. Open a terminal window at the purchaser gadget you propose on the usage of to log into your server and difficulty the command:
ssh-keygenYou may be requested to enter a filename in your newly generated key. To receive the default (/home/USER/.Ssh/id_rsa – where USER is your username), sincerely hit the Enter key. You will then be caused to kind and affirm a passphrase. Make this passphrase a sturdy one.
When the command completes, your key is ready to apply.
Copying Your Key to the Server
Now that you have your key on the equipped, it desires to be copied to the server you propose on logging into, through ssh. Fortunately, there’s a completely smooth manner to try this. Go returned to the terminal window you used to create the SSH Key and issue the command:
ssh-copy-id USER@SERVER_IPWhere USER is the username and SERVER_IP is the IP address of the server you need to log into. You’ll be brought on for the USER password. Once you correctly authenticate, the SSH Key might be copied and you could then log into the server inside the normal style. Issue the command (from the patron you used to create the SSH Key):
ssh USER@SERVER_IPBecause the client you are logging in from has the matching key this is now at the server, you’ll be logged in. Repeat this procedure on each customer machine that desires to SSH into the server.
Locking It Down
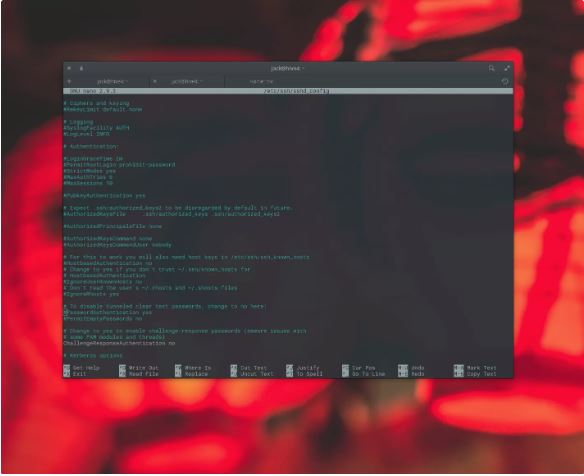
At this factor, customers can log into your server by using way of widespread SSH passwords or SSH Key Authentication. To make this setup even extra relaxed, you can save you using password authentication, with the aid of modifying the SSH daemon configuration. To try this, trouble the command:
sudo nano /etc/ssh/sshd_configIn that file, look for the line:
#PasswordAuthentication yesUncomment it out (get rid of the # image) and exchange sure to no.
Next, search for the road:
#PubkeyAuthentication yesUncomment out that line.
Save and close the report (hit Ctrl+x) and solution sure. Restart the SSH daemon with the command:
sudo systemctl restart sshdNow in case you try to SSH into that server from any customer that doesn’t comprise a matching SSH Key, you will be denied get admission to.
Where is the SSH Key Stored
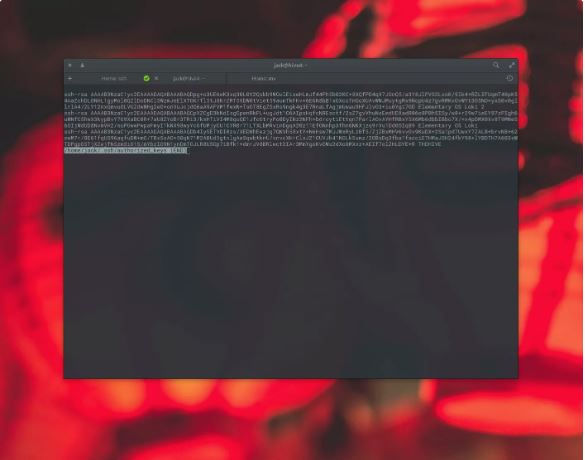
For individuals who are curious, log onto the server to which you copied your keys. Issue the command:
less ~/.ssh/authorized_keysThe output of the above command will display all the keys you’ve sent from clients (the use of the ssh-copy-identification command). If you discover you want to revoke SSH Key Authentication from a specific purchaser, you may delete the strains that correspond with the purchaser’s hostname (the hostname is the closing little bit of records inside the key).