Set Access Control Lists,Access Control Lists (additionally referred to as ACLs) are a function of the Linux kernel that allows to define extra high-quality-grained get right of entry to rights for files and directories than those distinct via regular ugo/rwx permissions.
For example, the standard ugo/rwx permissions does no longer allow to set special permissions for exclusive person customers or companies. With ACLs this is notably smooth to do, as we are able to see in this text.
Set Access Control Lists,Checking File System Compatibility with ACLs
To make certain that your record systems are presently supporting ACLs, you need to check that they have been mounted the usage of the acl option. To try this, we will use tune2fs for ext2/3/four file structures as indicated beneath. Replace /dev/sda1 with the tool or document machine you need to test:
# tune2fs -l /dev/sda1 | grep "Default mount options:"Note: With XFS, Access Control Lists are supported out of the container.
In the following ext4 file system, we can see that ACLs have been enabled for /dev/xvda2
# tune2fs -l /dev/xvda2 | grep "Default mount options:" 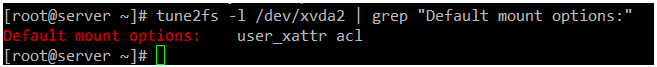
If the above command does not imply that the report gadget has been established with help for ACLs, it’s far maximum in all likelihood due to the noacl choice being present in /and so on/fstab.
In that case, put off it, unmount the report machine, and then mount it again, or definitely reboot your machine after saving the modifications to /and so on/fstab.
Set Access Control Lists,Introducing ACLs in Linux
To illustrate how ACLs paintings, we are able to use a group named developers and add users walterwhite and saulgoodman (sure, I am a Breaking Bad fan!) to it.:
# groupadd developers
# useradd walterwhite
# useradd saulgoodman
# usermod -a -G developers walterwhite
# usermod -a -G developers saulgoodmanBefore we proceed, allow’s confirm that both customers had been added to the builders institution:
# id walterwhite
# id saulgoodman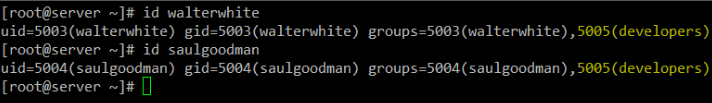
Let’s now create a listing known as check in /mnt, and a report named acl.Txt interior (/mnt/check/acl.Txt).
Set Access Control Lists,Then we can set the institution proprietor to builders and alternate its default ugo/rwx permissions recursively to 770 (accordingly granting read, write, and execute permissions granted to both the owner and the group proprietor of the file):
# mkdir /mnt/test
# touch /mnt/test/acl.txt
# chgrp -R developers /mnt/test
# chmod -R 770 /mnt/testAs predicted, you may write to /mnt/test/acl.Txt as walterwhite or saulgoodman:
# su - walterwhite
# echo "My name is Walter White" > /mnt/test/acl.txt
# exit
# su - saulgoodman
# echo "My name is Saul Goodman" >> /mnt/test/acl.txt
# exit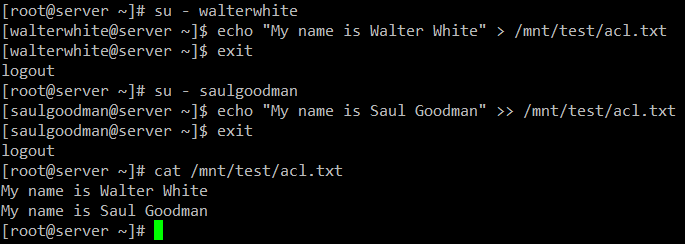
So a long way so accurate. However, we can soon see a trouble while we need to grant write access to /mnt/check/acl.Txt for another user that isn’t within the developers group.
Standard ugo/rwx permissions would require that the brand new consumer be introduced to the developers group, however that might deliver him/her the equal permissions over all of the gadgets owned by way of the organization. That is exactly where ACLs are available in accessible.
Setting ACL’s in Linux
There are types of ACLs: access ACLs are (which can be carried out to a record or directory), and default (optional) ACLs, which could handiest be implemented to a listing.
If documents interior a directory wherein a default ACL has been set do not have a ACL of their very own, they inherit the default ACL of their figure listing.
Let’s supply consumer gacanepa study and write get entry to to /mnt/check/acl.Txt. Before doing that, allow’s check the modern-day ACL settings in that directory with:
# getfacl /mnt/test/acl.txt Then alternate the ACLs on the file, use u: observed with the aid of the username and :rw to suggest study / write permissions:
# setfacl -m u:gacanepa:rw /mnt/test/acl.txt And run getfacl on the file again to compare. The following photo shows the “Before” and “After”:
# getfacl /mnt/test/acl.txt 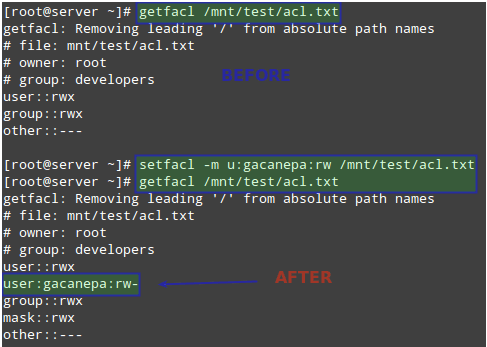
Next, we will need to give others execute permissions on the /mnt/test directory:
# chmod +x /mnt/test Keep in mind that so that you can get entry to the contents of a listing, a ordinary consumer needs execute permissions on that directory.
User gacanepa should now be able to write to the report. Switch to that user account and execute the subsequent command to verify:
# echo "My name is Gabriel Cánepa" >> /mnt/test/acl.txtTo set a default ACL to a listing (which its contents will inherit except overwritten otherwise), add d: earlier than the guideline and specify a directory in place of a file call:
# setfacl -m d:o:r /mnt/test
# getfacl /mnt/test/The ACL above will allow customers not within the proprietor group to have read access to the destiny contents of the /mnt/check listing. Note the difference inside the output of getfacl /mnt/test before and after the alternate:
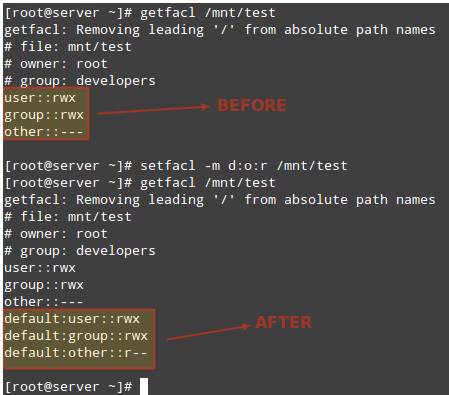
To remove a specific ACL, replace -m in the commands above with -x. For example,
# setfacl -x d:o /mnt/test Alternatively, you can also use the -b option to remove ALL ACLs in one step:
# setfacl -b /mnt/test For more statistics and examples on the usage of ACLs, please discuss with chapter 10, section 2, of the openSUSE Security Guide (additionally available for down load at no cost in PDF format).
Set Linux Disk Quotas on Users and Filesystems
Storage area is every other useful resource that need to be cautiously used and monitored. To try this, quotas may be set on a report gadget basis, both for person customers or for companies.
Thus, a restrict is placed at the disk usage allowed for a given consumer or a specific organization, and you may relaxation assured that your disks will no longer be stuffed to capacity by way of a slipshod (or malintentioned) user.
The first component you ought to do so as to permit quotas on a report machine is to mount it with the usrquota or grpquota (for user and group quotas, respectively) options in /and many others/fstab.
For instance, allow’s allow consumer-based quotas on /dev/vg00/vol_backups and group-primarily based quotas on /dev/vg00/vol_projects.
Note that the UUID is used to discover each report system.
Unmount and remount both file systems:
# umount /home/projects
# umount /home/backups
# mount -o remount /home/projects
# mount -o remount /home/backups Then check that the usrquota and grpquota options are present in the output of mount (see highlighted below):
# mount | grep vg00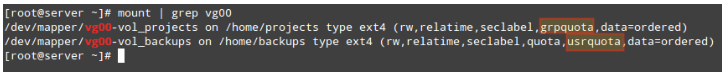
Finally, run the following commands to initialize and enable quotas:
# quotacheck -avugc
# quotaon -vu /home/backups
# quotaon -vg /home/projectsThat stated, allow’s now assign quotas to the username and organization we referred to in advance. You can later disable quotas with quotaoff.
Setting Linux Disk Quotas
Let’s begin by way of setting an ACL on /home/backups for user gacanepa, so as to deliver him examine, write, and execute permissions on that directory:
# setfacl -m u:gacanepa:rwx /home/backups/Then with,
# edquota -u gacanepaWe will make the gentle restriction=900 and the tough restriction=one thousand blocks (1024 bytes/block * 1000 blocks = 1024000 bytes = 1 MB) of disk area usage.
We also can region a limit of 20 and 25 as gentle and hard limites on the quantity of documents this user can create.
The above command will release the textual content editor ($EDITOR) with a brief file in which we are able to set the limits cited formerly:
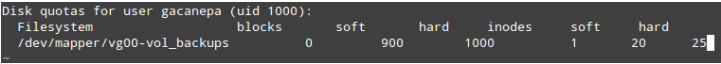
These settings will motive a warning to be shown to user gacanepa when he has both reached the 900-block or 20-inode limits for a default grace period of 7 days.
If the over-quota situation has no longer been eliminated by means of then (for example, via removing files), the soft limit will become the tough restrict and this person will be avoided from the usage of more storage space or developing more documents.
To test, let’s have user gacanepa attempt to create an empty 2 MB report named test1 interior /domestic/backups:
# dd if=/dev/zero of=/home/backups/test1 bs=2M count=1
# ls -lh /home/backups/test1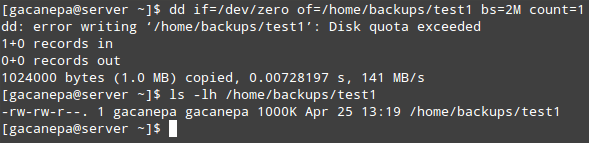
As you may see, the write operation report fails because of the disk quota having been exceeded. Since handiest the first one thousand KB are written to disk, the bring about this example will most probable be a corrupt file.
Similarly, you can create an ACL for the developers organizations in order to provide members of that institution rwx access to /home/tasks:
# setfacl -m g:developers:rwx /home/projects/And set the quota limits with:
# edquota -g developersJust like we did with consumer gacanepa in advance.
The grace length can be certain for any quantity of seconds, minutes, hours, days, weeks, or months through executing.
# edquota -tAnd updating the values below Block grace duration and Inode grace period.
As opposed to block or inode usage (which might be set on an user or organization-foundation), the grace length is ready device-extensive.
To report quotas, you could use quota -u [user] or quota -g [group] for a fast listing or repquota -v [/path/to/filesystem] for a more targeted (verbose) and nicely formatted report.
Of route, you will want to replace [user], [group], and [/path/to/filesystem] with precise user / group names and file gadget you need to check.
Summary
In this article we’ve got explained a way to set Access Control Lists and disk quotas for users and corporations. Using both, you may be able to manipulate permissions and disk usage greater successfully.
If you want to learn extra about quotas, you could consult with the Quota Mini-HowTo in The Linux Documentation Project.
Needless to mention, you may additionally anticipate us to answer questions. Just post them the usage of the remark shape below and we are able to be extra than happy to take a look.