Centralized Secure Storage using iSCSI Target, ISCSI is a block stage Protocol for coping with storage devices over TCP/IP Networks, in particular over long distances.
ISCSI goal is a far flung tough disk supplied from an far off iSCSI server (or) target.
On the opposite hand, the iSCSI patron is known as the Initiator, and will access the garage that is shared within the Target gadget.
The following machines had been utilized in this text:
Server (Target):
Operating System – Red Hat Enterprise Linux 7
iSCSI Target IP – 192.168.0.29
Ports Used : TCP 860, 3260Client (Initiator):
Operating System – Red Hat Enterprise Linux 7
iSCSI Target IP – 192.168.0.30
Ports Used : TCP 3260Step 1: Installing Packages on iSCSI Target
Centralized Secure Storage using iSCSI Target,To deploy the programs wished for the goal (we can address the customer later), do:
# yum install targetcli -yWhen the installation completes, we are able to start and enable the provider as follows:
# systemctl start target
# systemctl enable targetFinally, we need to allow the service in firewalld:
# firewall-cmd --add-service=iscsi-target
# firewall-cmd --add-service=iscsi-target --permanentAnd remaining however no longer least, we have to now not forget about to allow the iSCSI goal discovery:
# firewall-cmd --add-port=860/tcp
# firewall-cmd --add-port=860/tcp --permanent
# firewall-cmd --reloadStep 2: Defining LUNs in Target Server
Centralized Secure Storage using iSCSI Target, Before proceeding to defining LUNs inside the Target.
we want to create two logical volumes as explained in Part 6 of RHCSA series (“Configuring machine storage”).
This time we can name them vol_projects and vol_backups and location them interior a volume organization referred to as vg00, as proven in Fig.
1. Feel unfastened to pick the space allocated to each LV:
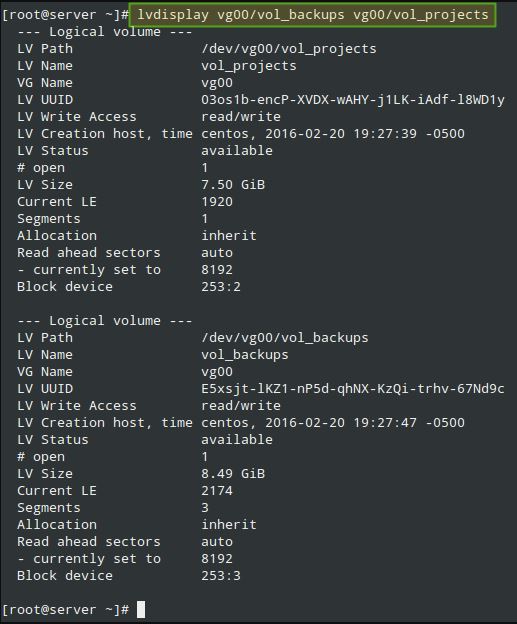
After growing the LVs, we’re prepared to define the LUNs within the Target with a view to make them to be had for the purchaser gadget.
Centralized Secure Storage using iSCSI Target, As proven in Fig.2,
we are able to open a targetcli shell and difficulty the subsequent instructions, so one can create two block backstores (nearby garage sources that represent the LUN the initiator will certainly use) and an Iscsi Qualified Name (IQN), a method of addressing the goal server.
Please confer with Page 32 of RFC 3720 for extra info on the structure of the IQN.
In unique, the text after the colon character (:tgt1) specifies the name of the goal, while the text earlier than (server:) suggests the hostname of the goal in the domain.
# targetcli
# cd backstores
# cd block
# create server.backups /dev/vg00/vol_backups
# create server.projects /dev/vg00/vol_projects
# cd /iscsi
# create iqn.2016-02.com.tecmint.server:tgt1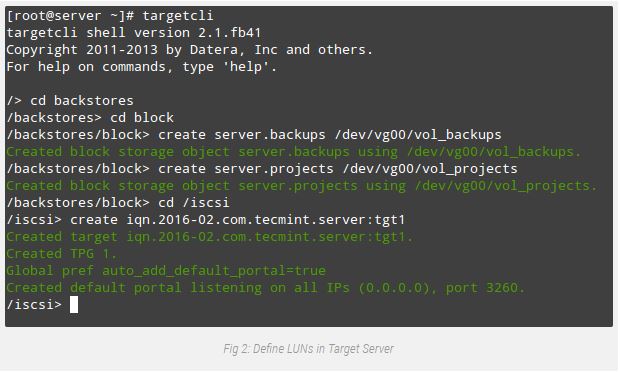
Centralized Secure Storage using iSCSI Target, With the above step, a brand new TPG (Target Portal Group) became created at the side of the default portal (a couple which include an IP cope with and a port that is the way initiators can attain the goal) listening on port 3260 of all IP addresses.
If you need to bind your portal to a particular IP (the Target’s most important IP, for example)
Delete the default portal and create a new one as follows (otherwise, bypass the following targetcli instructions.
Note that for simplicity we’ve got skipped them as nicely):
# cd /iscsi/iqn.2016-02.com.tecmint.server:tgt1/tpg1/portals
# delete 0.0.0.0 3260
# create 192.168.0.29 3260Now we’re prepared to proceed with the introduction of LUNs. Note that we’re the use of the backstores we previously created (server.Backups and server.Initiatives). This procedure is illustrated in Fig. 3:
# cd iqn.2016-02.com.tecmint.server:tgt1/tpg1/luns
# create /backstores/block/server.backups
# create /backstores/block/server.projects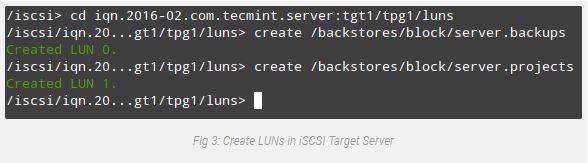
The remaining component inside the Target configuration includes growing an Access Control List to limit get entry to on a in step with-initiator foundation.
Since our patron device is called “consumer”, we will append that textual content to the IQN. Refer to Fig. Four for information:
# cd ../acls
# create iqn.2016-02.com.tecmint.server:client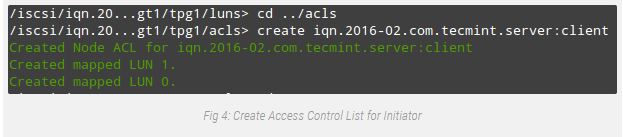
At this point we will the targetcli shell to show all configured sources, as we can see in Fig. Five:
# targetcli
# cd /
# ls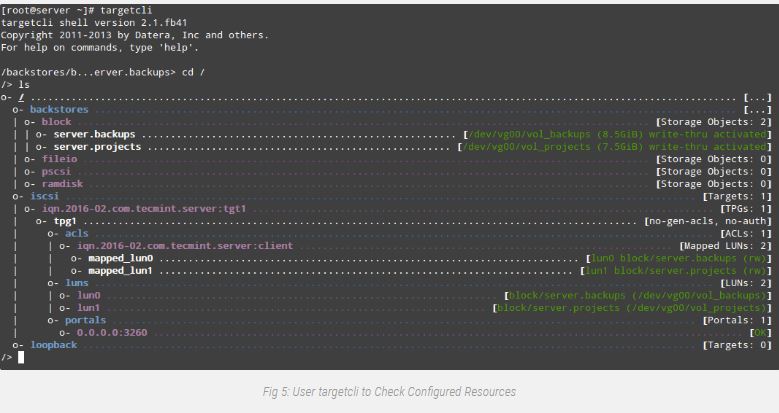
To give up the targetcli shell, truly type exit and press Enter. The configuration may be stored routinely to /and so forth/goal/saveconfig.Json.
As you may see in Fig. 5 above, we’ve a portal listening on port 3260 of all IP addresses as predicted. We can verify that the usage of netstat command (see Fig. 6):
# netstat -npltu | grep 3260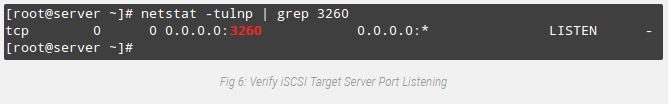
This concludes the Target configuration. Feel unfastened to restart the system and verify that each one settings continue to exist a reboot.
If not, make sure to open the essential ports within the firewall configuration and to begin the target service on boot. We are now ready to set up the Initiator and to connect with the consumer.
Step 3: Setting up the Client Initiator
In the purchaser we will want to put in the iscsi-initiator-utils package deal, which affords the server daemon for the iSCSI protocol (iscsid) in addition to iscsiadm, the management utility:
# yum update && yum install iscsi-initiator-utilsOnce the installation completes, open /etc/iscsi/initiatorname.Iscsi and update the default initiator call (commented in Fig. 7) with the call that was previously set in the ACL on the server (iqn.2016-02.Com.Tecmint.Server:client).
Then store the report and run iscsiadm in discovery mode pointing to the target. If a success, this command will go back the target statistics as proven in Fig. 7:
# iscsiadm -m discovery -t st -p 192.168.0.29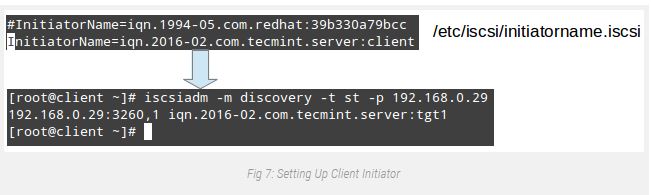
The next step is composed in restarting and permitting the iscsid provider:
# systemctl start iscsid
# systemctl enable iscsidAnd contacting the goal in node mode.
This must bring about kernel-degree messages, which when captured via dmesg display the device identity that the remote LUNs were given in the nearby system (sde and sdf in Fig. 8):
# iscsiadm -m node -T iqn.2016-02.com.tecmint.server:tgt1 -p 192.168.0.29 -l
# dmesg | tail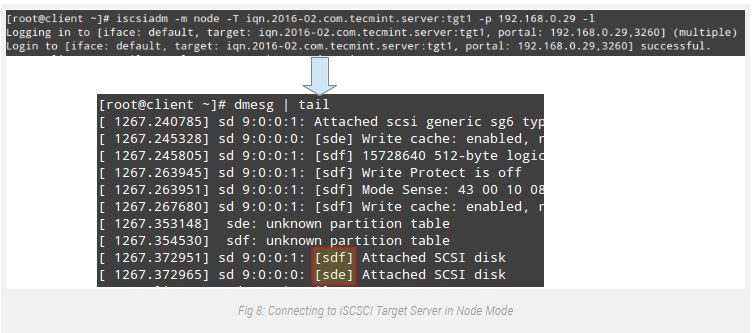
From this point on, you may create partitions, or maybe LVs (and filesystems on pinnacle of them) as you would do with some other storage device.
For simplicity, we are able to create a number one partition on each disk a good way to occupy its entire to be had space, and layout it with ext4.
Finally, let’s mount /dev/sde1 and /dev/sdf1 on /projects and /backups, respectively (be aware that those directories ought to be created first):
# mount /dev/sde1 /projects
# mount /dev/sdf1 /backupsAdditionally, you could add two entries in /etc/fstab so as for both filesystems to be set up automatically at boot the use of every filesystem’s UUID as back through blkid.
Note That the _netdev mount alternative need to be used to be able to defer the mounting of those filesystems until the network provider has been started out:
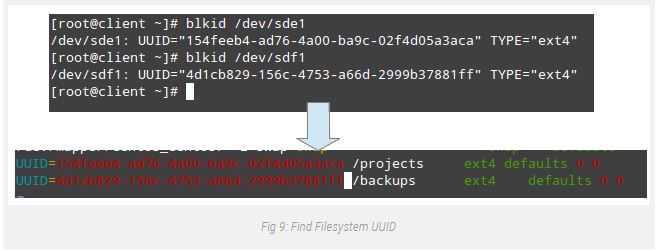
You can now use those devices as you will with any other storage media.
Summary
In this newsletter we’ve got covered the way to set up and configure an iSCSI Target and an Initiator in RHEL/CentOS 7 disitributions.
Although the first undertaking isn’t always a part of the specified abilties of the EX300 (RHCE) examination, it is wished with the intention to implement the second subject matter.
Don’t hesitate to let us understand if you have any questions or comments about this article – feel unfastened to drop us a line the usage of the comment form under.
Looking to setup iSCSI Target and Client Initiator on RHEL/CentOS 6, follow this guide: Setting Up Centralized iSCSI Storage with Client Initiator.




