Use SSH Key ,If you’re a Linux administrator, then you definitely are very familiar with the ssh command. Why? Because it’s far the maximum popular way of having access to a far flung Linux server. Out of the box, Secure Shell (SSH) is often considered pretty relaxed. If you’re serious approximately your security, but, you understand that to be a slight exaggeration. Yes, SSH is a long way higher than the use of maximum other means of remotely logging right into a Linux server. If used wisely, it can be made even more at ease. How? With SSH Key Authentication.
Use SSH Key What is Key Authentication?
Normally, whilst you log into a far off server with SSH, you achieve this using a username/password combination. Issue the command:
ssh [email protected]You’ll be induced for the consumer password for olivia. That’s the most customarily used technique for SSH logins. However, the use of a password is limited to the period of password you can keep in mind, or are inclined to kind out. Sure, you could have user olivia set a password that’s extraordinarily lengthy and complex, but is that user going to need to kind that password every time they want to login? Probably now not. With Authentication, an encrypted passphrase is used that is a ways longer than is sensible with a wellknown password. So the cryptographic strength located in Authentication goes manner beyond that which a popular password can healthy.
But to use SSH Key Authentication, you have to set it up. Fortunately, it’s tremendously smooth to do.
Generating Your SSH Key
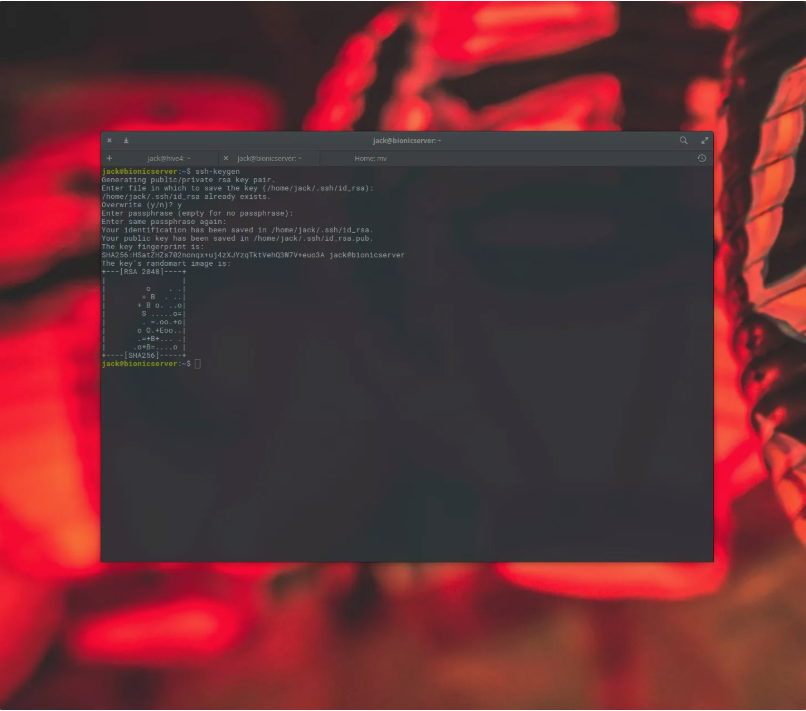
The first factor you must do is generate an SSH Key. This is pretty clean. Open a terminal window on the consumer device you plan on using to log into your server and issue the command:
ssh-keygen
You could be requested to enter a filename for your newly generated key. To accept the default (/home/USER/.Ssh/id_rsa – wherein USER is your username), absolutely hit the Enter key. You will then be prompted to kind and verify a passphrase. Make this passphrase a strong one.
When the command completes, your key is prepared to apply.
Copying Your Key to the Server
Now that you have your key at the equipped, it wishes to be copied to the server you plan on logging into, through ssh. Fortunately, there’s a completely smooth manner to try this. Go lower back to the terminal window you used to create the SSH Key and issue the command:
ssh-copy-id USER@SERVER_IP
Where USER is the username and SERVER_IP is IP deal with of the server you need to log into. You’ll be precipitated for the USER password. Once you correctly authenticate, the SSH Key may be copied and you can then log into the server inside the normal fashion. Issue the command (from the purchaser you used to create the SSH Key):
ssh USER@SERVER_IP
Because the client you’re logging in from has the matching key that is now on the server, you’ll be logged in. Repeat this process on every purchaser machine that desires to SSH into the server.
Locking It Down
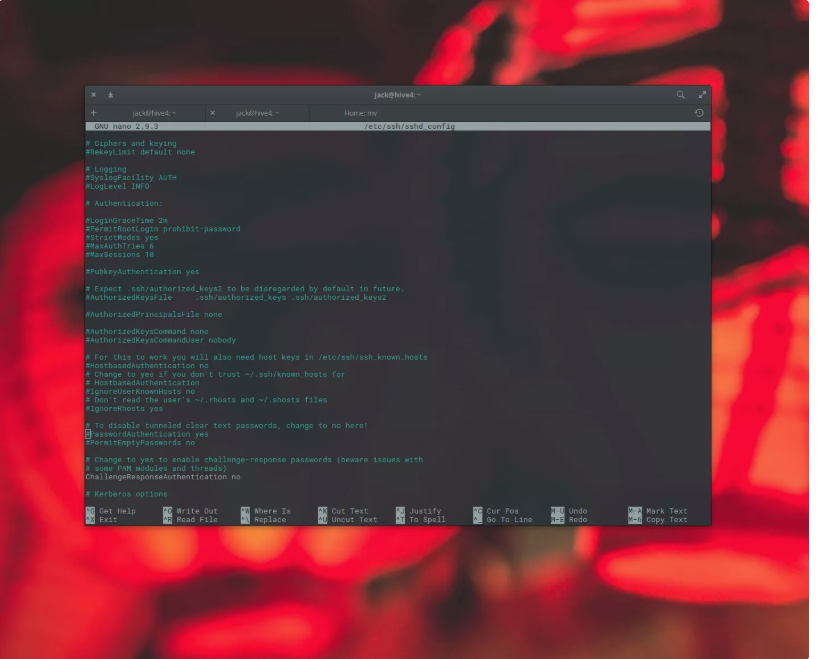
At this factor, users can log into your server by means of way of trendy SSH passwords or SSH Key Authentication. To make this setup even extra at ease, you may prevent using password authentication, via editing the SSH daemon configuration. To do that, issue the command:
sudo nano /etc/ssh/sshd_configIn that file, look for the line:
#PasswordAuthentication yes
Uncomment it out (remove the # symbol) and change yes to no.
Next, look for the line:
#PubkeyAuthentication yes
Uncomment out that line.
Save and close the file (hit Ctrl+x) and answer yes. Restart the SSH daemon with the command:
sudo systemctl restart sshd
Now if you attempt to SSH into that server from any client that does not contain a matching SSH Key, you will be denied access.
Where is the Key Stored
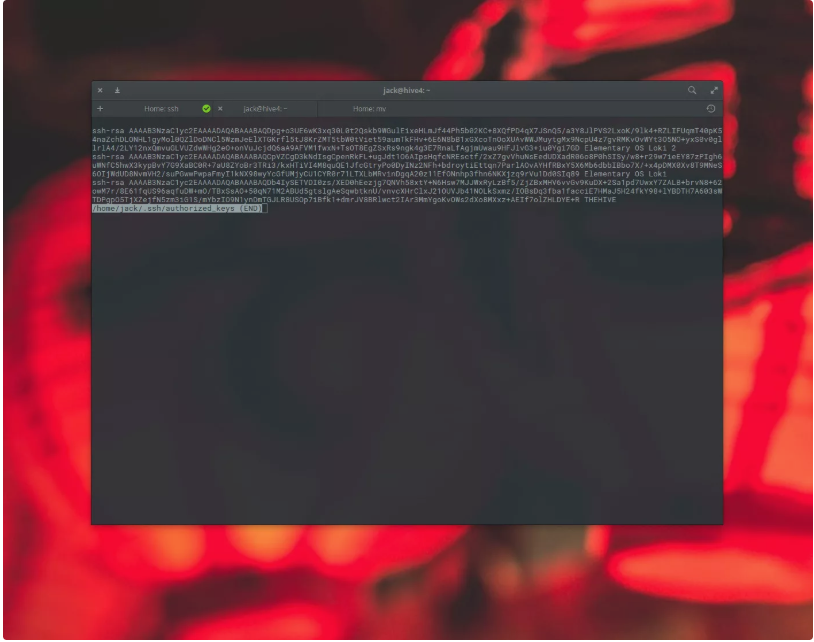
For those who are curious, log onto the server to which you copied your keys. Issue the command:
less ~/.ssh/authorized_keys
The output of the above command will display all of the keys you’ve sent from clients (using the ssh-copy-id command). If you find you want to revoke SSH Key Authentication from a particular client, you can delete the lines that correspond with the client’s hostname (the hostname is the last bit of information in the key).